Cyber risk management, made simple
Helping humans understand their information security risks and enabling them to take the right action.
SecurityStudio is a continuous cybersecurity risk management platform that allows decision-makers in the public sector, business leaders, and managed service providers (MSPs) to quickly identify the most immediate, pressing threats to their business and clients, and make confident, risk-informed decisions moving forward.
We like to keep things simple and easy to use. That’s why we designed our cyber risk management platform to do the heavy technical work of assessing, auto-reporting, and dynamically scoring your risk for you so you can maximize every minute of your time by addressing issues from the get-go.
Know exactly how much risk you have at any given time with one number. It is a true indication of how secure you are on a scale of 300-850 (runs familiar with your credit score). Compliance, defensibility, and insurability are outcomes of solid, continuous risk management—and we’re here to help you do this noble work.
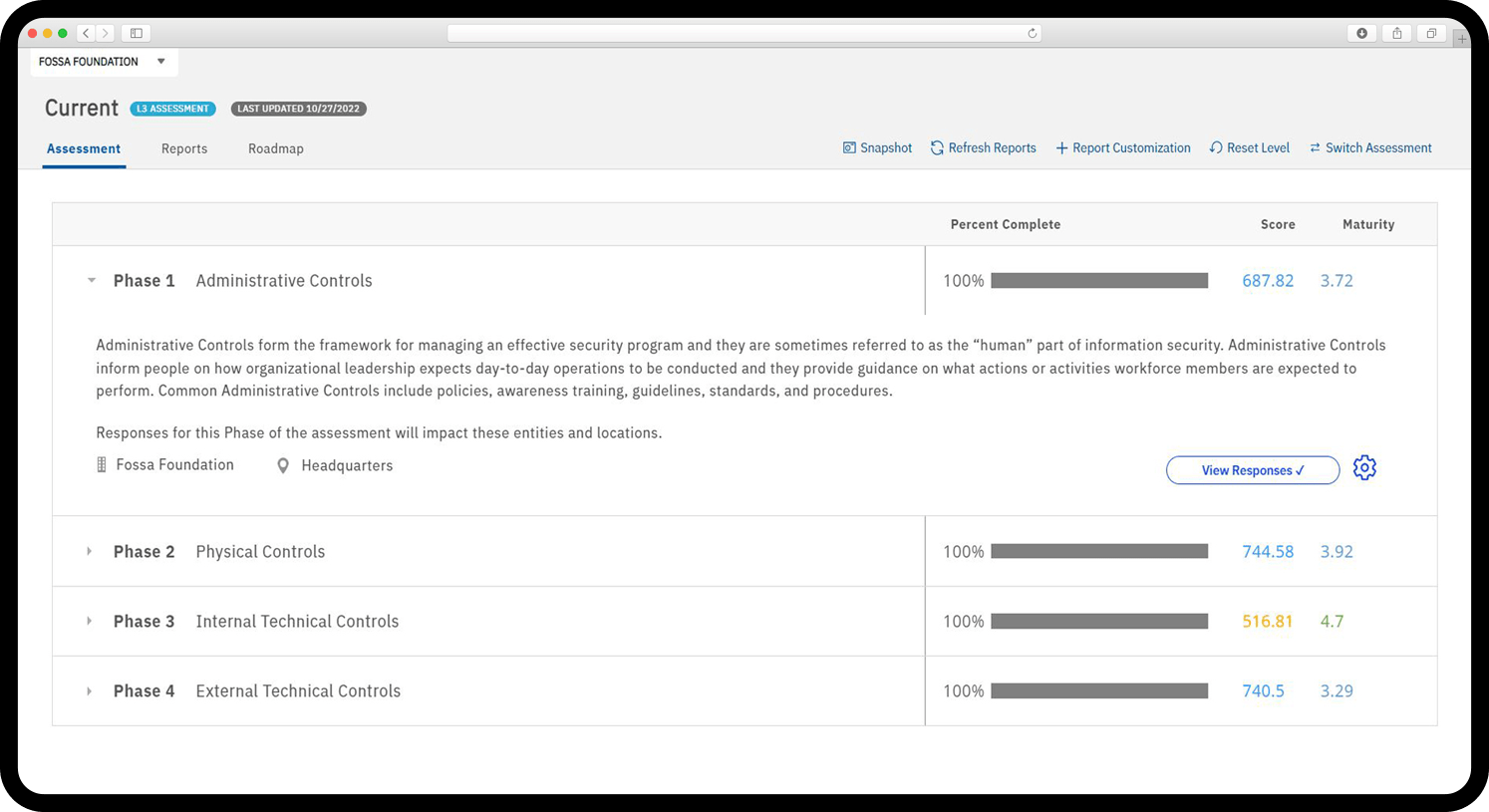
Auto-generating reports make it easy for you and your clients to communicate key security recommendations to different stakeholders and identify and prioritize risk to instill change.
Don’t suffer from blinky light syndrome. Focus on investing your money on the foundations of security before buying new technology.
When you don’t ask the right questions you don’t get the right answers. We give you a common sense, comprehensive assessment to easily diagnose all phases of your and your clients’ cybersecurity performance to effectively measure your cybersecurity posture.
We’re a small-but-mighty team of information security experts (i.e., tech-y folks) who geek out about quantifying cybersecurity risk and building software that makes it easy for organizations to get ahead of potential threats.
Objectivity and integrity mean a lot to us, which is why we created a platform that gives you all the information you need (and nothing you don’t).
Information Security
Policy Templates
Risk Assessments
(with No Strings Attached)
Specialty Reports
Smart, intuitive, and objective risk management software. Try us on for size.